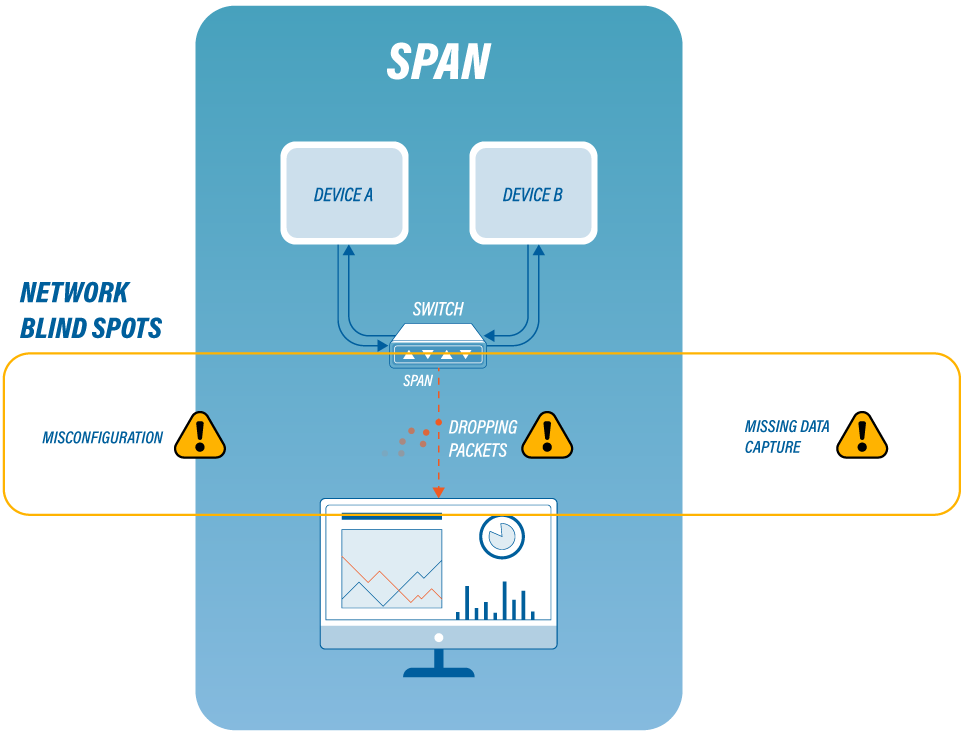
Network blind spots: TAPs vs SPAN ports
Network blind spots could be compared to a slow gas leak. They are hidden areas of the network that...
August
26,
2021
Read more



.png)


© 2026 Profitap HQ B.V. and its licensors. All Rights Reserved — Profitap HQ B.V., High Tech Campus 84, 5656 AG Eindhoven, The Netherlands | Privacy Policy | Terms and Conditions