Despite all your hard work to keep the network running smoothly all the time, still, things can go wrong. Let's face it. You can't blame the network every time for not working properly. When problems occur, you should be fully prepared with the knowledge and tools you need to tackle the issue. This means getting your hands dirty to dig deeper to search for potential network problems and troubleshoot the bottleneck issues immediately. Wireshark is often the go to tool used for packet level analysis.
Yet, there's a common challenge Network analysts would face, that is to pinpoint the actual information to look for in Wireshark as they often have to dig through large volumes of traffic. One way to do this is by using the filter engine that helps remove the noise from a packet trace and lets you see only the packets that interest you. Using filters in Wireshark is essential to get down to the data you actually want to see for your analysis.
Finding the right filters that work for you all depends on what you are looking for. Start with a gameplan and base your filters on that. However, it's always good to draw some inspiration from what other analysts use on their quest to find their packets of interest. Therefore, we've asked Network Analysts from all over the world who are experts in their fields to share the Wireshark filters they use the most. Hopefully they will make your life a bit easier!

Betty DuBois
Betty DuBois is the Chief Detective for Packet Detectives, LLC, an application and network performance consulting firm based in Atlanta, GA. She has been solving mysteries since 1997. Experienced with a range of hardware and software capture solutions, she captures the right data, in the right place, and at the right time to find the real culprit.
tcp.stream eq ${tcp.stream} and (tcp.analysis.window_update or tcp.analysis.zero_window)
This will show the time between a TCP window zero and the recovery. Be sure to color code the tcp.analysis.zero_window, but not the tcp.analysis.window_update to make them easy to spot.
dns.flags.rcode eq 0 and dns.time gt .1
This will show slow DNS responses, the question is it your local DNS resolver or due to recursion?
 Chris Greer
Chris Greer
Chris Greer supports clients in several regions of the USA, Latin America, and the Caribbean. He assists IT professionals in resolving the root cause of network and application performance problems. He also develops and delivers Network Analysis and Troubleshooting courses featuring analyzers such as Wireshark.
For me - off the bat it is not always easy to spotlight exactly what IS involved in a problem, but I know what is NOT involved. So one of the filters I like to use is what I call a NOT filter template. What this filter does is start with some basic things that I am reasonably sure are not involved in the problem, and as I exonerate different conversations and protocols, I just add them to the list. So here is an example if I want to get rid of the background static like broadcasts and layer 2 protocols. I label this filter “No Background/Chatter"
!(eth.dst == ff:ff:ff:ff:ff:ff or arp or stp)
From there, as I find conversations or even whole subnets that I identify as not a part of what I am looking for (this is pretty common when I am looking at huge, unfiltered traces) I can remove them as I go and see what is left.
Example:
!(ip.addr == 23.0.0.0/8 or ip.addr == 173.0.0.0/8 or ip.addr == 172.0.0.0/8 or ip.addr == 17.0.0.0/8 or arp)
These types of filters allow me to whittle down a trace file when I don’t know exactly what I am looking for and don’t want to over-filter before I am sure.
 Jasper Bongertz
Jasper Bongertz
Jasper Bongertz is a Senior Technical Consultant for Airbus Defence and Space CyberSecurity. He started working freelance in 1992 when he began studying computer science at the Technical University of Aachen, eventually moving to Airbus to focus on IT security, Incident Response, and Network Forensics. He runs a blog about network analysis topics called blog.packet-foo.com.
tcp.flags.syn==1 or tcp.flags.fin==1 or tcp.flags.reset==1 or dns or tls.handshake.type==1 or tls.handshake.type==2 or tcp.port==3389 or tcp.port==22 or tcp.port==445
This will help you to get a quick picture of the most important things happening in an incident response situation. The idea is to see all connections start and end as well as TLS certificates and full details on RDP, SSG and SMB sessions, plus DNS.
"This is what I usually use for captures on Internet uplink to see if there's anything going on that shouldn't be there."
 John Modlin
John Modlin
John worked as a weapons systems specialist in the Navy on ballistic computers, inertial navigation systems, airborne integrated systems, and simulation systems. Since then he has worked on networks in I.T. for a myriad of government entities and private firms, analyzing issues in large networks with some 40,000+ users. In 1999, John attended Sniffer University and started solving problems with packet analysis and Ethereal®. He then certified with Wireshark (WCNA).
ip and (ip[1] & 0xfc) >> 2 == 0x20 || ip and (ip[1] & 0xfc) >> 2 == 0x22
Capture traffic with the Assured Forwarding flag set, to check QoS is correctly being applied to video traffic.
udp[1] & 1 != 1 && udp[3] & 1 != 1 && udp[8] & 0x80 == 0x80
When VOIP traffic isn’t isolated to a separate vlan tag that you can use to capture with, but you still need to capture just VOIP traffic to analyze.
 Megumi Takeshita
Megumi Takeshita
Megumi Takeshita, known as Packet Otaku, runs a packet analysis company after having worked as a network analyst at BayNetworks and Nortel Networks for many years. Ikeriri Network Service is a reseller of Riverbed, Metageek,
wlan.addr_resolved contains Nintendo
Are you tired of entering 6bytes HEX values to filter a station?
You can easily use OUI name instead of MAC address, in this case, you can find your game consoles in your wireless network. You can also filter using eth.addr_resolved contains Sony in your wired network too. And OUI is always installed with your Wireshark, so, you do not need to edit manuf or ethers configuration.
arp.duplicate-address-frame
When there is a problem in your network and the users say that their IP addresses are already used, you can simply put this filter string to check the duplicated IP addresses. You also check the sender MAC address of ARP announcement too.
http.request.uri contains string(ip.dst)
If you want to look for client's direct web access packets for intranet. This means the full request URI (HTTP Host header+URI) contains the local IP address of the destination host, it may be valuable to filter out HTTP requests via proxy.
 Phill Shade
Phill Shade
Phill is an Innovative IT and Security Professional with over 31 years of practical experience in diverse networking and technological areas. He is an innovative IT and Security Professional with over 31 years of practical experience in diverse networking and technological areas. Phill has extensive knowledge in all aspects of network and security analysis, design, troubleshooting, optimization, and administration.
Low Orbit Ion Cannon: frame matches "(?i)probando"
I was recently working a case of a client that suspected e was being attacked, but the packet structure didn't match the usual DDoS patterns. If fact it turned out to be an old school malware tool borrowed from the Anonymous collective: Low Orbit Ion Cannon
Sec - ARP Bogus Requests (Man in The Middle?) (Custom) not RFC 4436: (arp.opcode == 1) && !(eth.dst == ff:ff:ff:ff:ff:ff)
A common WiFi hack in Man-in-the-Middle, often done with basic ARP Poisoning. ARP poisoning can be difficult to notice given the floods of ARP in normal networking. However, the giveaway for most ARP Poisoning scripts is the testing mechanism that they use to verify the Poison has succeeded.
 Sake Blok
Sake Blok
Sake has been analyzing packets for over 15 years. While working for a reseller of networking equipment, he discovered many bugs in devices from multiple vendors and presented his findings to the vendors to fix the issues. In 2009, Sake started the company SYN-bit to provide Network Analysis and troubleshooting services to enterprises with a complex IT infrastructure.
tcp.flags&7 || (tcp.seq==1 && tcp.ack==1 && tcp.len==0) || tcp.len>1
This will show all SYN/FIN/RST packets (tcp.flags&7), the final ACK of the 3-way-handshake (tcp.seq==1 && tcp.ack==1 && tcp.len==0) and all data packets (tcp.len>0, but I started using 1 to skip the TCP KeepAlive packets).
tcp.stream == ${tcp.stream} as a filter button
This will show the full TCP stream of the selected packet by clicking on the filter button. I used to do this by following TCP stream and then closing the content window. The filter button is quicker and easier.
 Stuart Kendrick
Stuart Kendrick
Stuart has functioned as both ITIL Problem Manager and Problem Analyst, provided 3rd tier support, and contributed to design efforts. Specializing in transport, monitoring, and packet analysis, he provides mentoring and communication training, teaches Root Cause Analysis workshops, and coordinates the efforts of multiple groups interacting with multiple vendors to solve problems or design solutions. He also runs skendric.com.
eth.ig==1
Grabs a particular bit out of the first byte – if this particular bit is ‘1’, then the frame is a multicast (which includes broadcasts). This then leads to a discussion of the function of the first byte in a frame and how it is constructed, e.g. things like OUI and, well, the least significant bit.
not eth.ig==1
Hides multicasts, including broadcasts, for instance displays only unicasts
eth.addr==ff:ff:ff:ff:ff:ff
Displays only broadcasts (but not other multicasts and of course not any unicasts)
not eth.addr==ff:ff:ff:ff:ff:ff
Hides broadcasts, for instance displays other types of multicasts and unicasts
"Sometimes, I want to toggle the appearance of multicast and broadcast frames where I want my students to explore the distinctions between unicast, multicast, and broadcast (where of course, we sometimes thinking of broadcast as a subset of multicast … and sometimes we want to focus on it as a separate beast).”
 Tom Tosh
Tom Tosh
Tom founded CHI Metrix (“
"Is it the VPN tunnel, a firewall, or something else that's breaking the application connection between a workstation and a hosted application hundreds of miles away?"
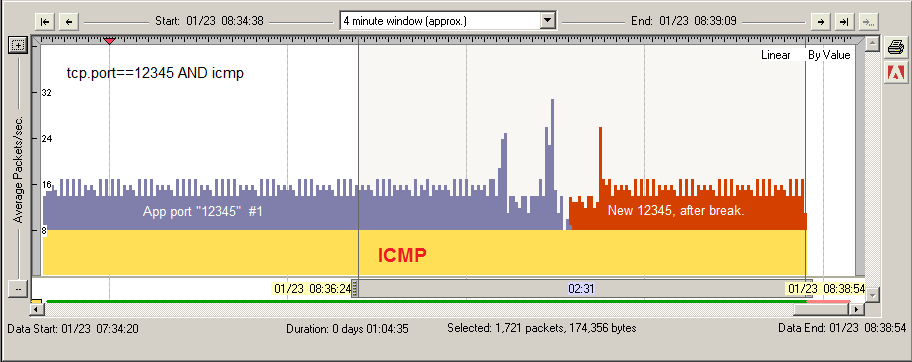
tcp.port==12345 AND icmp
First set up basic pings between the two and wait for the problem. Assuming the application runs over TCP port 12345.
Don't forget to check The Evolution of Portable Packet Capture Solutions article if you want to learn more about a portable network capture solution that flawlessly integrates with Wireshark or have a look at other Wireshark Filters that our engineers use.

