Lessons from aviation safety
Imagine boarding a plane knowing that if something went wrong, no one would know why. There is no flight data recorder, cockpit voice recorder, or way to reconstruct events. Air travel would be a gamble, with every incident a mystery. A miscalibrated sensor, an engine issue, or a pilot error could go unchecked and unlearned. Aviation safety would rely on guesswork rather than evidence.
Now compare that to your network. Like an aircraft, it’s a complex system where a multitude of components must work together seamlessly: firewalls, routers, applications, servers, users, etc. When things fail, the consequences may not necessarily be lives lost, but they can still be costly. Transactions stall, applications crash, or security breaches slip through unnoticed. Without proper visibility, your team is flying blind.
Everyday network failures
Packet capture is often only discussed in the context of cybersecurity and forensic investigations, but in reality, many of the most frustrating and expensive network issues aren’t malicious: they result from misconfigurations, compatibility problems, or performance bottlenecks.
Take a misconfigured firewall as an example. An overly strict outbound rule might block legitimate traffic from a business-critical application. Suddenly, your users are complaining that they “can’t connect”, but logs don’t tell you why. With full packet capture, you can see the blocked sessions, verify handshake attempts, and pinpoint the exact rule causing disruption. Without it, you might waste hours tweaking unrelated settings or escalating to the wrong team.
IOTA: your network’s flight recorder
IOTA, our full-fidelity packet capture solutions, work like flight data recorders for digital infrastructures. It records every packet at line rate, timestamps, and has no packet loss. This allows both security and network operations teams to:
- Reconstruct incidents precisely for compliance and legal purposes.
- Perform root cause analysis for operational issues.
- Detect subtle anomalies or evasive threats that logs may miss.
- Provide hard evidence to external stakeholders, auditors, or regulators.
- Monitor performance trends to preempt issues before they escalate.
- Baseline your network.
Model options at a glance
- IOTA EDGE (1G/10G): Portable TAPs with in-line and out-of-band capture, hardware filters/slicing, SSD storage. In compliance with industry safety standards, the IOTA 1G M12 version meets the EN 45545-2 safety standards for fire. The M12 connectors make it easy to connect IOTA with standardized equipment. M12 connectors are compact, rugged, and suitable for harsh environmental conditions such as vibrations, temperature fluctuations, and moisture, making them ideal for moving vehicles.
- IOTA CORE (10G/100G): High-speed, high-performance capture and analysis for core and data center links.
- IOTA CM: Centralized management and multi-segment analytics across all deployed IOTAs.
| IOTA EDGE (1G/10G) | IOTA CORE (10G/100G) | IOTA CM |
 |
 |
 |
|
Small/mid-size enterprises, small branches, and small data centers
|
Core networks, large branches, and data centers
|
Centralized management application
|
Performance monitoring with IOTA
Full-fidelity packet capture isn’t just about detecting threats, it’s also about performance monitoring. Packets reveal the truth of how your applications behave in real-world conditions:
- Latency analysis: Identify whether slowness originates at the client, server, or somewhere in transit. Here is a screenshot of the IOTA TCP analysis dashboard:
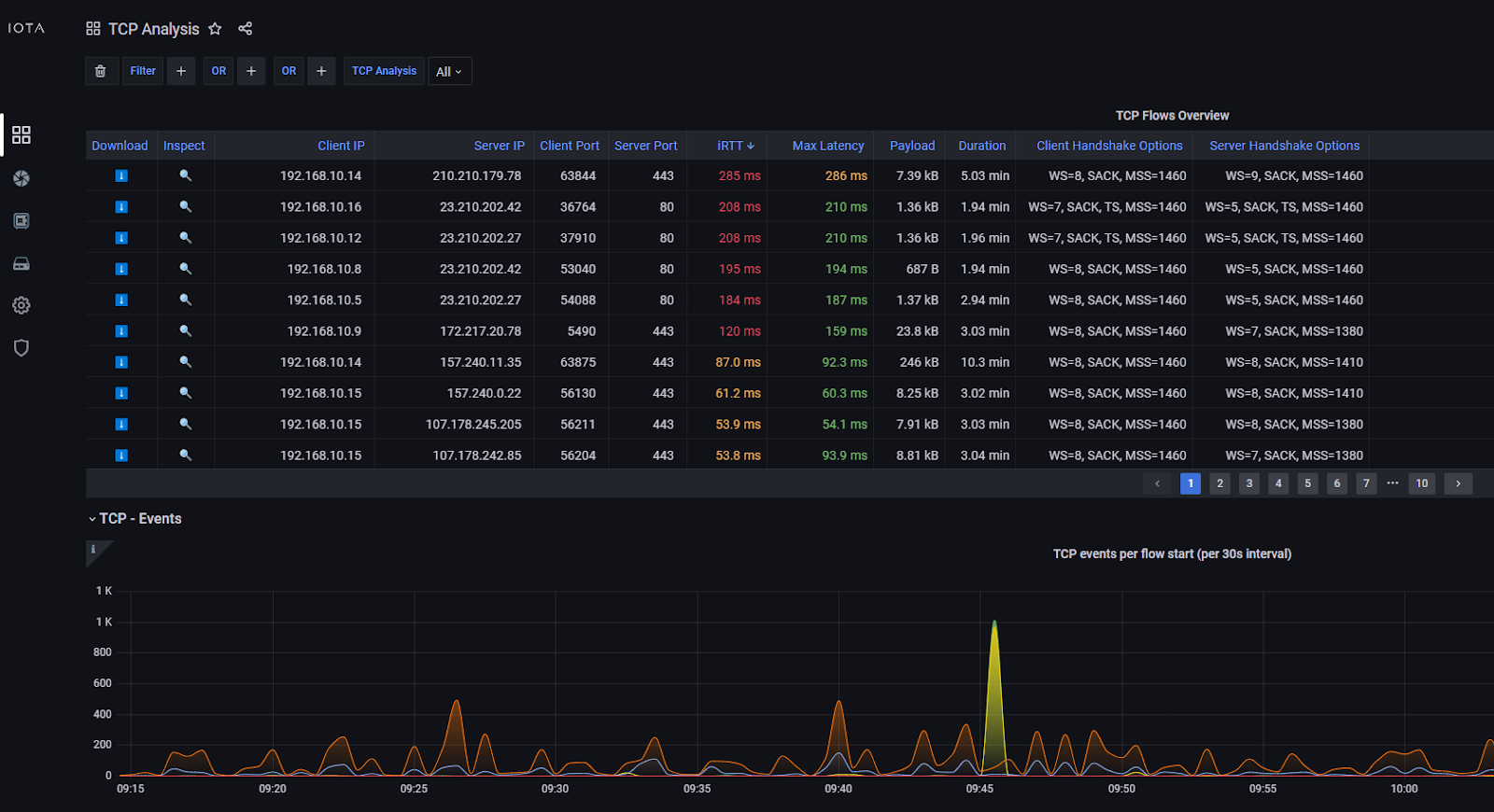
- Throughput tracking: See how much data is actually moving, not just what logs say.
- Protocol behavior: Spot anomalies like excessive retransmissions, handshake failures, or dropped packets.
- User experience insights: Confirm whether complaints about “the network” are rooted in infrastructure issues or application inefficiencies.
Just as aviation uses black box data to enhance both safety and efficiency, networks can use packet data not only for post-incident investigation but also for proactive performance optimization.
Conclusion: don’t fly blind
Aviation’s black boxes are not optional, they are critical safety measures. Networks deserve the same treatment. Without comprehensive packet capture, your forensic capabilities are limited, your troubleshooting is slowed, and your risk increases. By deploying full-fidelity packet capture solutions, you empower your organization to investigate, remediate, and prevent both security incidents and performance failures effectively.
Don’t gamble with your network. Install a black box.