We are just in the first quarter of 2018 and already a new wave of DDoS attacks hit companies across the globe. In January, for example, the Dutch Tax Authority together with some of the most important financial institutions in the Netherlands were hit by a number of cyberattacks that left their customers unable to use their mobile or online banking applications for hours at a time.
March come, and the first ever 1.3 terabits per second DDoS hit Github platform with all its force, using an unconventional and sort of new type of attack, called memcached DDoS attack. Another 1.7Tbps attack happened almost right after the Github one (just one week later) and it was against an anonymous company in the US, according to Arbor Networks.
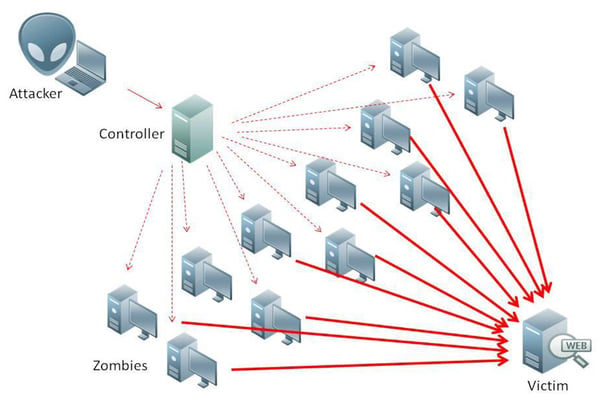 Image by Ludovic via Privacy Canada
Image by Ludovic via Privacy Canada
They were both record breaking attacks that paved the way to the terabit era, reminding us once again that not only DDoS attacks continue to be a huge threat, but they are also finding new ways to disrupt networks and systems.
With this kind of increase in virtual threats, preventing or mitigating a DDoS attack has never been more important.
Evolution of DDoS Attacks
Things have changed a lot since the first ever DDoS attack in 1974 orchestrated by a 13-year old student from US or since the days when some kids attempted to take control on an IRC channel by using simple-bandwidth DoS attack.
Nowadays, hackers are using a technique called reflection amplification. It increases the amount of malicious traffic that can be used against different companies.
When your network is used in a DDoS attack or, even worse, gets hit by it, your business reputation can be damaged, your network can perform poorly, and your productivity level can decrease.
In the last 5 years, the ability to turn small requests into “amplified” responses completely changed the Distributed Denial of Service attack landscape. This amplification technique was the reason why we saw a massive increase in DDoS attacks size lately.
We have now evolved from attack exploiting NTP servers and bots that can use large amounts of network bandwidth to DNS reflection/amplification attacks. As stated above, a terabit attack already happened that used open memcached servers. These are open source and free caching systems that help speed up your networks and website.
They are proving to be very effective due to the memcached servers high-bandwidth access links, and, thus, becoming increasingly popular in high-bandwidth reflection/amplification DDoS attacks.
The rapid increase of the so called memcached DDoS attacks indicates that they have been already weaponised, and it’s now broadly used by attackers within a relatively short interval.
Risk Prevention and Mitigation: Network Monitoring Tools
 Even though the DDoS defense and internet infrastructure industries have made significant progress on DDoS mitigation, there are companies out there that still struggle every day.
Even though the DDoS defense and internet infrastructure industries have made significant progress on DDoS mitigation, there are companies out there that still struggle every day.
The latest DDoS attacks showed us just how important is to have the right security tools in place. And in order for these security appliances to do their job properly, you need a highly-efficient network access solution that stands between them and your network. Because every DDoS prevention and mitigation strategy should always start at the very bottom - the packet level.
In other words, highly-efficient network monitoring hardware, like our own network TAPs, troubleshooters or NPBs, transfer the right information to your security tools so that your company can be as protected as possible against the next DDoS attacks.
Our data center network TAPs and Network Packet Brokers complement your security tools. How? By providing all the data these tools need in order for your network engineers to make a complete and accurate analysis.
An end-to-end visibility platform (as the one showcased in the white paper below) makes it easier to monitor device activity, sings of disruptions or red flags – all warnings that your network is being used in an attack.
By having access to the right data, network admins can keep track on what's happening over the network in real-time (for example, random spikes in traffic that exceed normal patterns) or perform an accurate forensics analysis to help them understand what triggered the attack in the first place.
Interested in finding out more about cybersecurity and why is such a challenge these days? Then read this article.
That being said, we can’t stress enough just how important is to have the right monitoring tools for an advanced DDoS mitigation strategy. They provide the ultimate benefit by helping you recognise the signs of a DDoS attack right before it actually happens, so that you can take the necessary actions as soon as possible.

