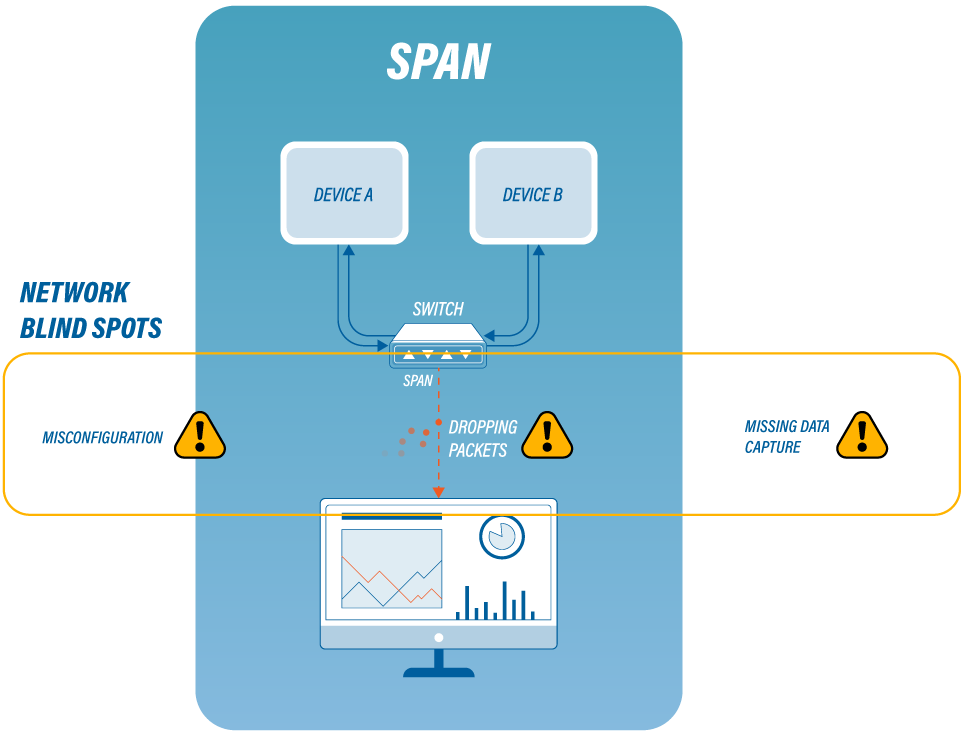
Network blind spots could be compared to a slow gas leak. They are hidden areas of the network that negatively impact the network’s performance because they will not show up in routine analysis. When data between certain segments in a network cannot be analyzed or seen, “blind spots” occur, where the causes of network performance and dangerous security issues might reside.
Without due diligence to prevent blind spots and proper network monitoring infrastructures, critical environments like Industrial Control Systems (ICS) can face potential device failures, performance issues, unhappy users and customers, compliance problems, and even serious cybersecurity threats.
To begin with, port mirroring, also known as SPAN or roving analysis, is a method of monitoring network traffic that forwards a copy of each incoming and/or outgoing packet from one or more port (or VLAN) of a switch to another port where the network traffic analyzer is connected. SPAN is often used on simpler systems to monitor multiple stations at once.
Another common way of accessing monitoring data is through a Test Access Port (TAP): a purpose-built device that makes a copy of network data but does not alter the data and does not require any programming for installation. In contrast, SPAN ports do require configuration to the switch (or switches) every time you want to edit the SPAN ports’ settings.
SPAN ports can have measurable effects on network traffic leading to Network Blind Spots issues, including:
SPAN port shortages: SPAN ports are often in short supply for monitoring purposes. They can also be easily misconfigured, resulting in incorrect or missing data captures.
SPAN port overloading: SPAN ports can drop packets if the switch's CPU gets overloaded. This can drastically reduce the effectiveness of performance and security monitoring.
Improper SPAN port programming: resulting in incorrect or missing data captures.
Network TAPs provide a way to access the data flowing across a network in order to forward it to network security and performance monitoring tools. TAPs are hardware devices deployed at key locations between two points in network infrastructure, such as routers, switches, or firewalls, where data access is needed for monitoring or troubleshooting purposes.
Let's start by exploring two types of TAPs:
- Aggregation TAPs (Many:1) connect multiple network ports to one monitoring port (M:1), combining all incoming traffic streams into a single flow of outgoing traffic.
- Regeneration TAPs (1:Many) copy the traffic from a single incoming traffic stream to multiple outputs, allowing the monitoring of a single network line by multiple analyzers.
TAPs copy traffic either to a single monitoring tool or, more often, to a network packet broker that services multiple QOS testing tools, network monitoring tools.
Additionally, there are different types of TAPs depending on the type of medium, including fiber optic TAPs and copper TAPs. Both types provide an exact copy of the traffic to the network traffic analyzer, while the main signal continues uninterrupted. For fiber optic TAPs, the light beam is split in two, while in the copper system, the electrical signal is copied.
TAPs can also handle full packet captures and carry out deep packet inspections for protocol, non-compliance, intrusions, etc. Because of this, TAP data is admissible in a court of law as evidence, whereas SPAN port data are not.
Security is another area where there are differences between the two technologies. SPAN ports are often configured for unidirectional traffic, but they can also receive traffic in some instances, creating a critical vulnerability. Conversely, TAPs cannot be addressed, have no IP address, and therefore cannot be hacked.
There are some aggregation TAPs, like Profitap Booster SPAN, for example, that can aggregate eight 10/100/1G ports to one 1G-10G output. The Booster can also insert VLAN tags to ingress packets. This way, the source port information of each packet is forwarded to the analyzer.
The table below shows a comparison in terms of functionality of SPAN vs TAP.
|
Functionality Analysis SPAN vs TAP |
||
|
TAP |
SPAN |
|
|
Access to monitoring packets |
|
|
|
Achieve complete access and visibility across your physical and virtual networks |
|
|
|
Obtain fail-safe, permanent in-line network access to live traffic in high-speed networks |
|
|
|
Protect the network link availability for in-line security tools |
|
|
|
Eliminate the risk of single points of failure in accessing the network traffic |
|
|
|
Deliver lossless traffic aggregation from multiple in-line links or out-of-band connections |
|
|
SPAN ports can be used as a last resort, but when speed and reliable access to all your network data are crucial, TAPs are the best choice.
On heavier traffic networks, the security, capacity, and reliability of TAPs will bring complete visibility into the traffic on your network without worrying that packets are being dropped.

